So you’re on a domain-joined Windows machine, and someone tells you to “just submit the CSR to the CA.” Cool. One problem: You have no idea where the CA is. Or if there’s even one available. 😅
Fear not, fellow IT traveler — in this post, I’ll show you exactly how to:
- 🌐 Discover available Enterprise CAs in your domain
- 🛠️ Use PowerShell to list them automatically
- 📜 List all published certificate templates from a selected CA
Let’s get sleuthing 🔍
Option 1: Use certutil to Discover CA Servers
certutil -config - -ping
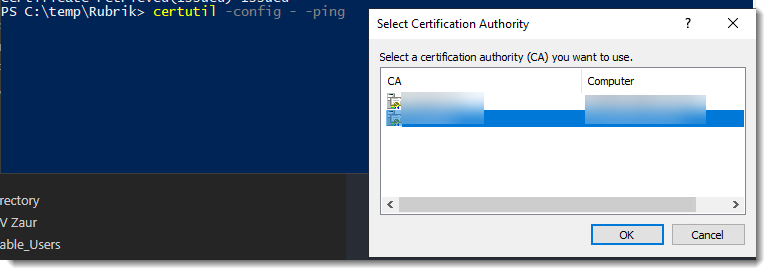
What it does:
- Lists all Enterprise Certificate Authorities published in Active Directory.
- Prompts you to select one if multiple are found.
- Also pings the selected CA to verify connectivity.
Once you select a CA from the Select Certification Authority window you’ll get output like this:
FQDN\CAServer
Connecting to FQDN\CAServer ...
Server "<your CA server>" ICertRequest2 interface is alive (125ms)
CertUtil: -ping command completed successfully.You just discovered your friendly neighborhood CA 🎉
Option 2: Use PowerShell to Find CA Info Automatically
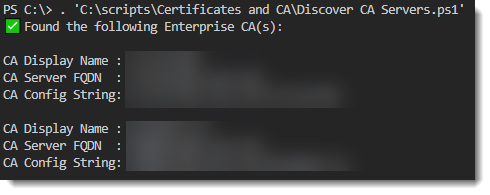
Here’s a PowerShell script you can run to get the CA name, the server that runs it, and the full config string:
# Discover Enterprise CAs in Active Directory
try {
$searchBase = ([ADSI]"LDAP://RootDSE").configurationNamingContext
$caPath = "CN=Enrollment Services,CN=Public Key Services,CN=Services,$searchBase"
$CAs = Get-ADObject -Filter 'objectClass -eq "pKIEnrollmentService"' -SearchBase $caPath -Properties dNSHostName, Name
if ($CAs) {
Write-Host "✅ Found the following Enterprise CA(s):`n"
foreach ($ca in $CAs) {
Write-Host "CA Display Name : $($ca.Name)"
Write-Host "CA Server FQDN : $($ca.dNSHostName)"
Write-Host "CA Config String: $($ca.dNSHostName)\$($ca.Name)"
Write-Host ""
}
} else {
Write-Warning "No Enterprise CA found in Active Directory."
}
}
catch {
Write-Error "Failed to query Active Directory for CA information. $_"
}
Why this is cool:
- You don’t need to guess or open the CA console.
- You get a clean config string to use in commands like
certreqorcertutil.
How to List Available Certificate Templates from a CA
Once you know the CA, you can list all the published templates it supports using this:
List Templates with certutil:
To view templates available on your domain CA server just run the following command:
certutil -templateYou can pipe the output to findstr to narrow down the search to template names as this:
certutil -template | findstr -i TemplatePropCommonName
'Or
certutil -template | findstr -i TemplatePropFriendlyName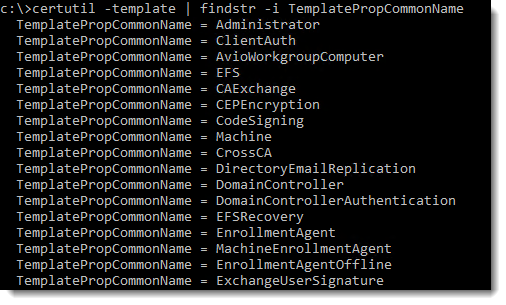
Pro Tip:
Use the internal name (WebServer, User) in your CSR submission:
certreq -attrib "CertificateTemplate:WebServer" -submit myrequest.csr
Optional GUI Way (If You’re Feeling Clicky)
- Open
certsrv.msc(on a server with CA role) to see published templates. - Open
certtmpl.mscto view all templates — not just published ones.
Final Thoughts
Whether you’re setting up HTTPS for an app like Rubrik, deploying SCEP for mobile devices, or just poking around, knowing how to discover your CA and its templates is pure IT wizardry.
✅ Use certutil if you’re in a hurry.
💻 Use the PowerShell script if you like automation.
📜 Use certutil -template to find which certificate types you can request.
